Administrator Guide
Requirements
U2F devices work only with a secure HTTPS connection. If you want to use U2F devices - make sure that your instance using it.
Reset an administrator's account
Should you ever lose your U2F device or secret codes, we provide two solutions to reset an administrator account:
- Another administrator should login and reset 2FA settings for the colleague.
- Reset 2FA settings directly by accessing the database:
- Connect to your database using a database management tool with the fields, as described in the Database connection fields.
- Identify the USER_AUTH_SETTING table in your database. This table is named AO_<hash>_USER_AUTH_SETTING where <hash> is a 6 digit hash value. (e.g. AO_BCCD15_USER_AUTH_SETTING).
- Execute SQL script where user is your username in Jira:
DELETE FROM AO_BCCD15_USER_AUTH_SETTING WHERE USERID IN (SELECT ID FROM APP_USER WHERE USER_KEY = 'user');
Disable U2F for Jira plugin
Should you ever change secure connection (HTTPS) to unsecure (HTTP), we provide a solution to disable plugin:
- Connect to your database using a database management tool with the fields, as described in the Database connection fields.
- Execute the SQL script:
DELETE FROM PROPERTYENTRY WHERE PROPERTY_KEY = 'authEnable';
Navigation
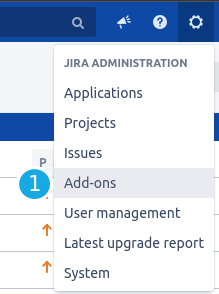
2FA (U2F / TOTP) Secure Login for Jira is located in the admin area (add-ons tab).
- Click on and select Add-ons. You will redirect to the Atlassian Marketplace.
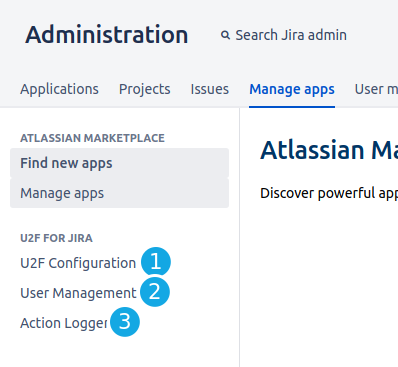
- Click on “U2F Configuration” to change plugin settings.
- Click on “User Management” to reset auth settings for a concrete user.
- Click on “Action Logger” to see all relevant actions
Configuration
Before using U2F for Jira you need to install and enable it in the Universal Plugin Manager. Also, enable it in own configuration. All base and additional settings are explained below.
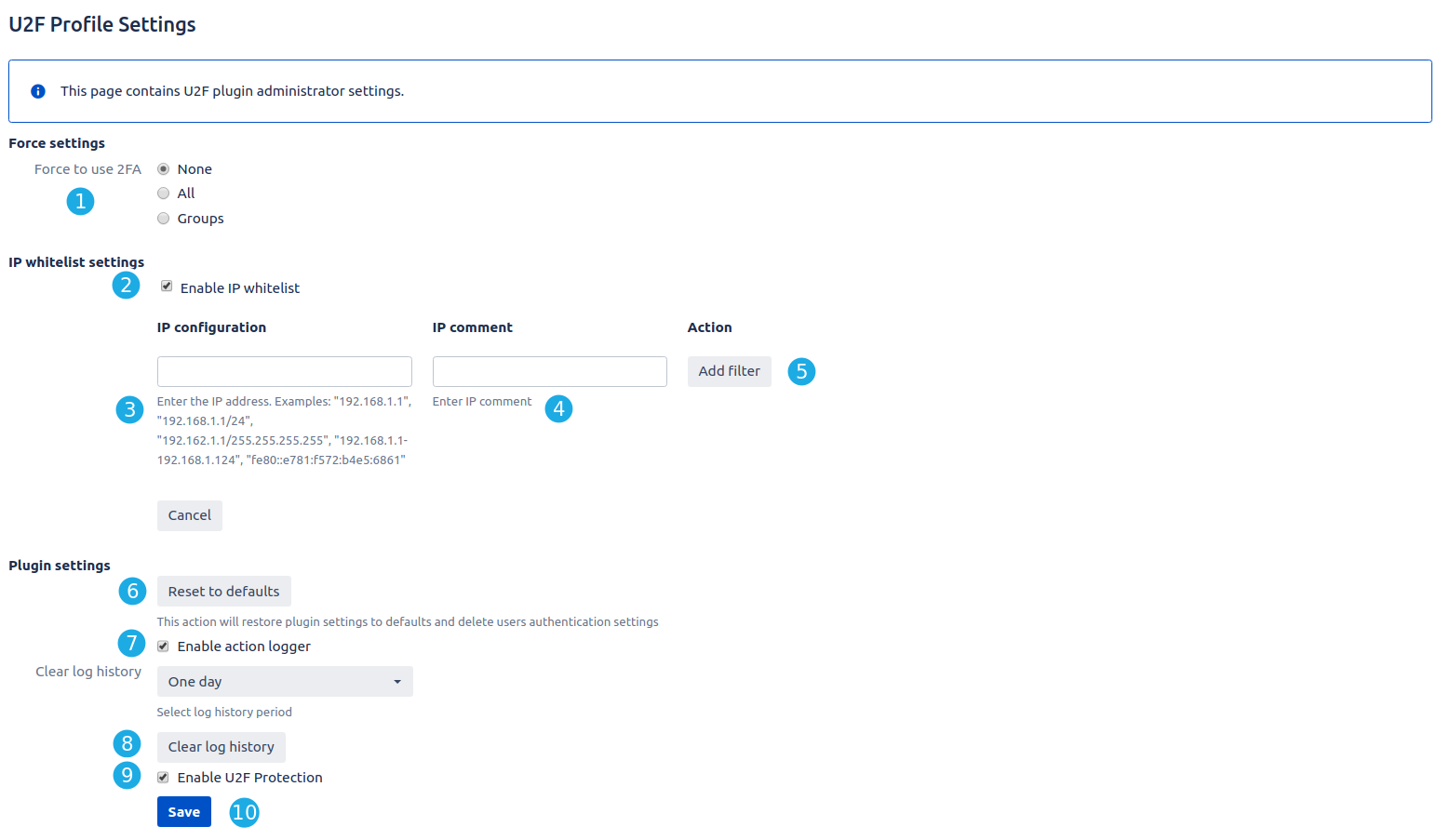
- It’s force setting for 2FA:
- None - 2FA not necessarily for Jira users. If you need to make it compulsory - use
- All - it’s compulsory for all users
- Groups - it’s compulsory only for selected groups.
- Mark the checkbox Enable IP whitelist to enable whitelist of IP addresses that pass without 2FA check.
- Enter the desired IP address.
- Enter the IP comment to recognize the IP address from the list. (not required)
- Click the Add filter button to add IP to whitelist.
- Reset to defaults. This action will restore plugin settings to defaults.
- Mark the checkbox Enable action logger to allow logging all action with 2FA. For example: adding or remove the device, log it into the system with U2F device.
- Clear log history. Select the log history period and clear logs.
- Mark the checkbox Enable U2F Protection to turn on the plugin.
- Click the Save button to save the configuration.
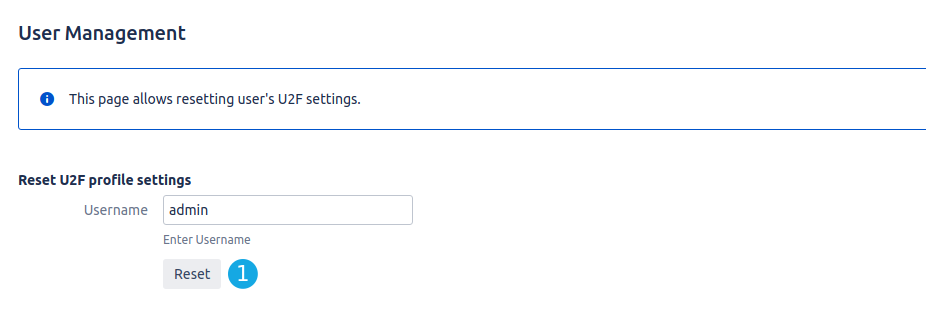
User Management
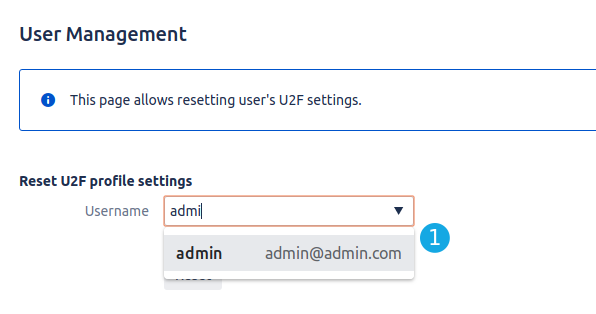
The User manager using to reset 2FA settings for a concrete user. This is necessary when a user lost device and reserve codes.
- You will see all users (username with email address) based on username which you type. Find the user from the dropdown and select it.
- Click on "Reset" to reset settings.
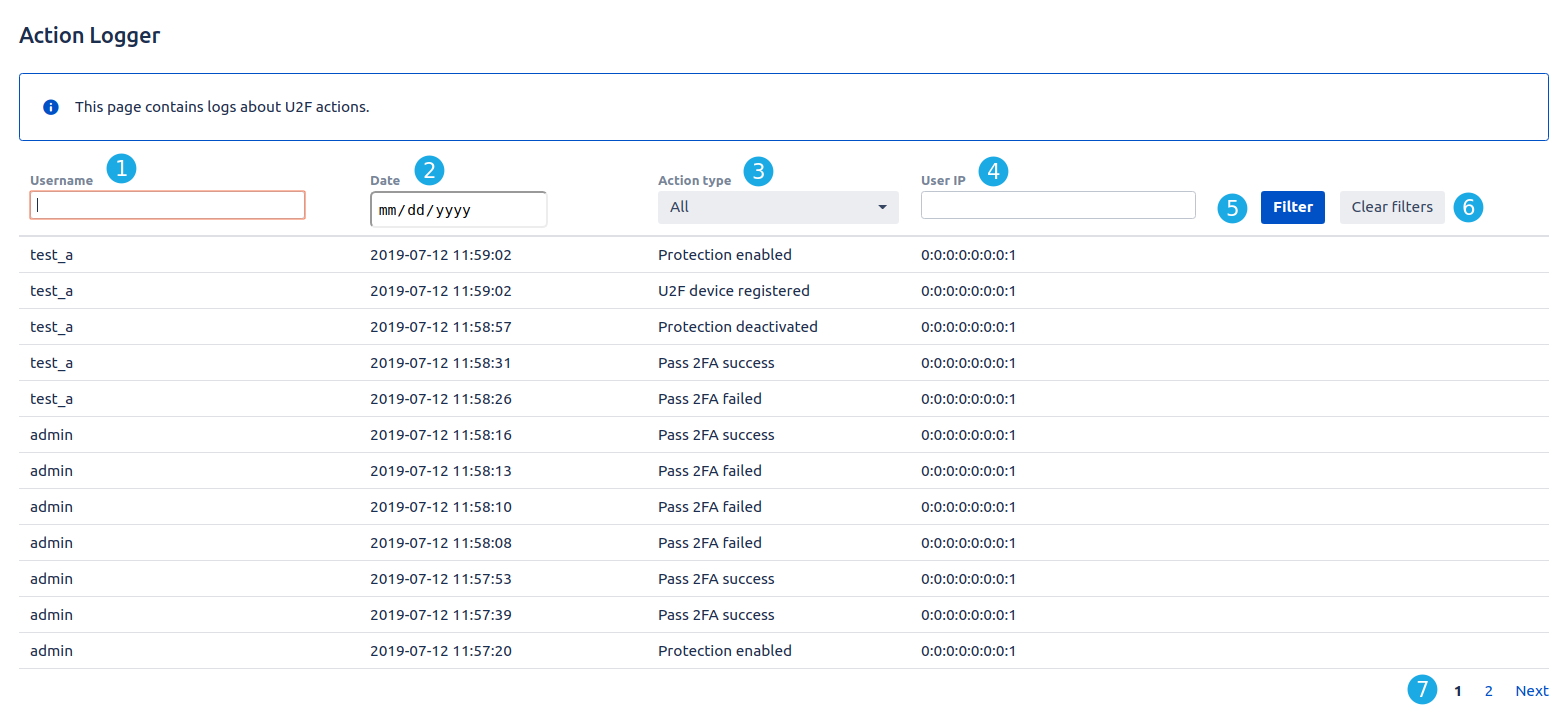
Action logger
We logged all relevant actions of U2F for Jira. It's accessible for administrators only: you can easily find out which user has logged in or registered and when.
- It's username column. Type letters into input.
- Date for a certain action. Select a date.
- Action type stores all relevant actions.
- User IP.
- Click "Filter" to filter logs.
- Clear filter.
- Use navigation to see more results.